# LDAP Basics and Configuration
The LDAP functionality is integrated to 4App Core Engine from version 4.4.
For lower Core Engine versions, the following separate 4Apps are required:
- Core Engine 4.0 to 4.3: Authentication Provider LDAP (opens new window)
- Core Engine 3.10 or below: Authentication Base (opens new window) and Authentication Provider LDAP (opens new window)
Before upgrading to Core Engine version 4.4, note the following:
- Remove the installed 4Apps
Authentication BaseandAuthentication Provider LDAP - Existing configurations will work as before and do not need to be changed.
If you worked with 4App Authentication Provider LDAP 4.0.1 or lower, check existing LDAP providers in the admin snap-in. If Login type is set to Active directory, field User filter should only contain additional and restriction(s) if required. Empty this field to only use filter from the backend (user search filter details).
# LDAP Basics
The LDAP integration in the 4ALLPORTAL allows to access directory services using the LDAP protocol. This makes it possible to log in to the 4ALLPORTAL with a user identity that is stored centrally in the directory service (e.g. in Microsoft Active Directory). This is not only faster, but also more secure.
At the first login to the 4ALLPORTAL, the data stored for a user in the directory service is used to automatically create a user in the 4ALLPORTAL.
Use admin snap-in Authentication/LDAP provider for configuration.
# Supported LDAP Servers
The LDAP functionality has been tested with the following directories:
- Microsoft Active Directory
- Lotus Domino
- Novell eDirectory
- OpenLDAP
Other directory services based on the LDAP protocol are possible.
# App Extensions
We offer two optional extensions for the Authentication Provider LDAP:
Authentication Service SSO (opens new window) enables Single Sign-on (SSO) for Windows Active Directory (AD) users. Users logged in to the Windows domain will be logged in to the 4ALLPORTAL automatically.
LDAP Sync User (opens new window) transfers all or selected users from your LDAP directory service to the 4ALLPORTAL and create them as new users.
# LDAP Configuration
Prerequisite: Make sure that you can access the directory service server (LDAP URL and port) from your 4ALLPORTAL server.
To configure an LDAP authentication provider, use admin snap-in Authentication/LDAP provider in the administration area. All changes made here will be stored in an XML file in folder custom/global/authentication_provider/ldap. The name of the XML file is the name you give your connector when you configure it.
# Basic Configuration Fields
The first part of fields (from Provider name to Language mapping as well as URL after logout) is our general authentication configuration.
Basic Authentication Configuration
For general authentication information and further configuration options (default provider or login screen), refer Core Engine's basic authentication provider documentation.
# LDAP Configuration Fields
The second part of fields is LDAP specific:
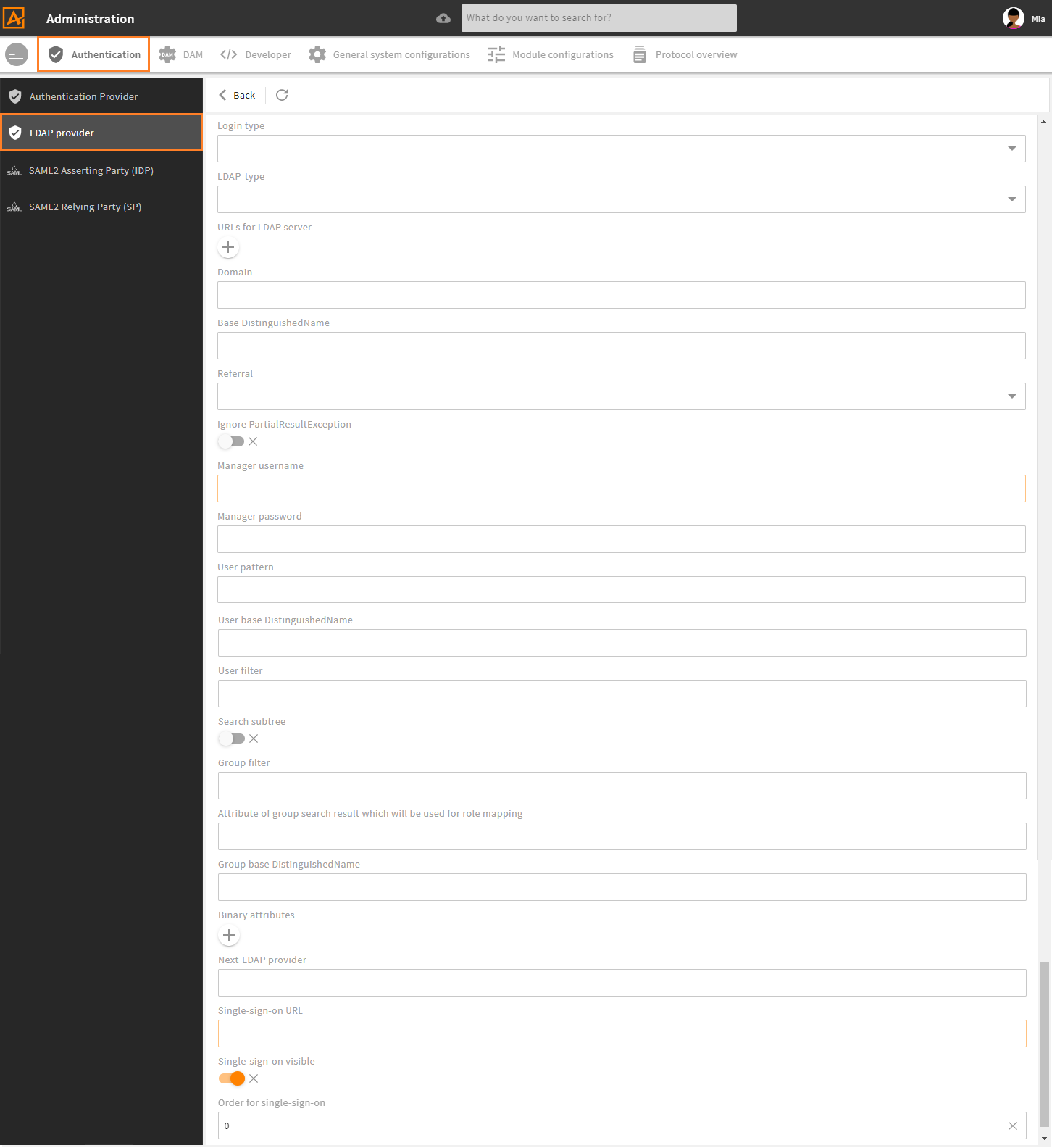
| Field | Attribute | Type | Description |
|---|---|---|---|
| Login type | login_pattern_type | enum LoginPatternType values: - default- user_pattern- manager- active_directory | Defines which parameters will be used: Pattern type details |
| LDAP Type | resolve_ldap_type | enum ResolveLdapType values: - active_directory- global_catalog | Only for login_pattern_type active_directory. When set, the first URL in urls is used to get the next LDAP URL with type active_directory or global_catalog from the Windows server. |
| URLs for LDAP server | urls | String[] | Assign URL(s) and port (optional) to LDAP server. Example: ldap://localhost:389 |
| Domain | domain | String | Only for login_pattern_type active_directory. Builds bindUser with user from request + “@” + domain for login with Down-Level Logon Name. |
| Base DistinguishedName | base | String | Entry point for accessing the LDAP directory. |
| Referral | referral | String | Set to follow if you want LDAP referrals to be followed. Allowed values: null, ignore (default, if value is null) and follow |
| Ignore PartialResultException | ignore_partial_result_exception | boolean default: false | Set to true if PartialResultException is thrown (which happens if Active Directory is used and LDAP tries to follow referrals). |
| Manager username | manager_user | String | Assign the manager username used to determine the bind user name for the LDAP user. Necessary if not possible to login with content from request, e.g. SSO, or if the user from request has not sufficient permissions |
| Manager password | manager_password | String | Assign the password for the manager_user |
| User pattern | user_pattern | String | Used when login_pattern_type = user_pattern. Replace login name from request in user_pattern from configuration to generate bind user.Example: uid={0},dc=example,dc=com |
| User base DistinguishedName | user_search_base | String | Searches users only below this path in LDAP directory. Example: dc=example,dc=com. Path must be set relative to the Base DistinguishedName path. |
| User filter | user_search_filter | String | Search pattern for user search. For type active_directory, take a look here |
| Search subtree | search_subtree | boolean default: false | Searches for users only in user_search_base. If true searches also in subtrees |
| Group filter | group_search_filter | String | Filter to find user groups for role mapping. Example: (&(objectclass=group)(member={0})) |
| Attribute of group search result | group_search_result | String | Content of attribute from group search will be used for role mapping to CoreEngine roles. Generated attribute dn is always possible. - cn: common name (short group name) - dn: distinguished name (full group name) - other attributes from group result also possible |
| Group base DistinguishedName | group_search_base | String | Searches only for groups below this directory entry. Example: dc=example,dc=com |
| Binary attributes | binary_attributes | String[] | These LDAP attributes have to be transferred binary. Needed for example when an OpenLDAP is used as a proxy for an Active Directory. |
| Next LDAP provider | next_provider | String | Order of LDAP authentication providers to try if a login is not possible with the current provider |
| Single-sign-on URL | single_sign_on_url | String | URL to Authentication service SSO application (opens new window) which allows single sign-on for Active Directory users. Has to start with http(s):// |
| Single-sign-on visible | single_sign_on_visible | boolean default: true | Set to false if SSO should not be shown in login GUI. Like visible, but for SSO provider only. |
| Order for single-sign-on | single_sign_on_order | int | Position on authentication provider list in login GUI. Like order, but for SSO provider only. |
- After your configuration is complete, reload your system.
- Your 4ALLPORTAL login page now contains one icon for LDAP login and (if
single_sign_on_urlis set) a second icon for SSO login.
# Pattern Type Details
Descriptions for the pattern types (Login types) to choose from:
# default
- search user filter:
user_search_filterfrom LDAP configuration - search for username: from request
- bind user: from request
- bind password: from request
# user_pattern
- search user filter:
user_search_filterfrom LDAP configuration - search for username: from request
- bind user: user from request replaced in user_pattern from LDAP configuration
- bind password: from request
# manager
- search user filter:
user_search_filterfrom LDAP configuration - search for username: from request
- bind user: manager_user from LDAP configuration
- bind password: manager_password from LDAP configuration
# active_directory
- username with @ (userPrincipalName)
- search user filter:
(&((userPrincipalName={0})(samAccountType=805306368){CUSTOM_FILTER})) - searchUser: username from request
- bind user: from request
- bind password: from request
- search user filter:
- username with (Down-Level Logon Name)
- search user filter:
(&((sAMAccountName={0})(samAccountType=805306368){CUSTOM_FILTER})) - searchUser: part before
\from username in request - bind user: from request
- bind password: from request
- search user filter:
- all other logins (sAMAccountName)
- search user filter:
(&((sAMAccountName={0})(samAccountType=805306368){CUSTOM_FILTER})) - searchUser: username from request
- bind user: username from request + “@” +
domainfrom LDAP configuration - bind password: from request
- search user filter:
Find more details, and an example search filter for Active Directory here.
# Login Screen
You have three options to display an authentication provider on your login screen:
- Let users choose from all configured and visible authentication providers (Microsoft Active Directory, Domino, eDirectory ...).
- Set one username/password provider that will additionally be called when entering 4ALLPORTAL credentials.
- Predefine one chosen provider that displays/logs in per default.
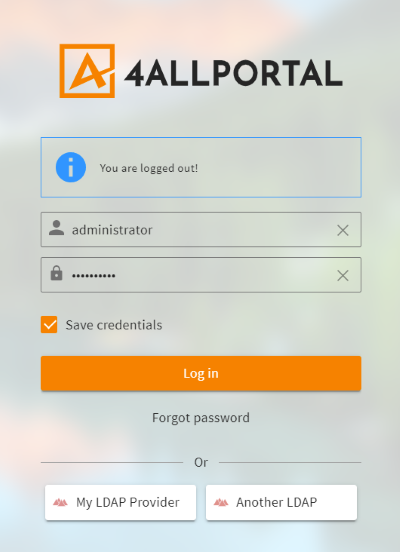
Login screen with two LDAP providers to choose from
# Customize Login Screen (Optional)
# Set Icon for Login GUI
To configure the displayed icon, just replace or copy your custom SVG file GLOBAL-AUTHENTICATION_PROVIDER-{$provider_name}.4apicon to folder custom/global/styles/default/.
# Set Locale for Login GUI
- locale keys for LDAP
L-GLOBAL-CONNECTOR-{$provider_name}L-GLOBAL-CONNECTOR-{$provider_name}-INFO
- locale keys for SSO
L-GLOBAL-CONNECTOR-{$provider_name}_SSOL-GLOBAL-CONNECTOR-{$provider_name}_SSO-INFO
# LDAPs Support
There is no special support for LDAPs, but it can be used with certificates in default java keystore.
# Reference: Example Configuration File
<authentication_provider>
<visible>false</visible>
<order>10</order>
<ignore_frontend_language>false</ignore_frontend_language>
<default_role_id>...</default_role_id>
<default_language></default_language>
<sync_to_contact>false</sync_to_contact>
<user_mapping>
<atr ce="firstname" extern="givenname"/>
<atr ce="ext_id" extern="objectSid" overwrite="false"/>
<atr ce="email" extern="mail"/>
<atr ce="username" extern="userPrincipalName"/>
<atr ce="lastname" extern="sn"/>
</user_mapping>
<group_role_mappings>
<group_role_mapping>
<prio>1</prio>
<group>CN=Admin,DC=example,DC=com</group>
<role>Admin</role>
</group_role_mapping>
<group_role_mapping>
<prio>100</prio>
<group>CN=Users,DC=example,DC=com</group>
<role>User</role>
</group_role_mapping>
</group_role_mappings>
<language_mapping>
<language>
<extern>Deutsch</extern>
<ce>de_DE</ce>
</language>
<language>
<extern>English</extern>
<ce>en_US</ce>
</language>
</language_mapping>
<login_pattern_type>active_directory</login_pattern_type>
<!-- get LDAP URL by first URL only for AD or GC -->
<!-- values: null, active_directory, global_catalog -->
<resolve_ldap_type>global_catalog</resolve_ldap_type>
<!-- values: LDAP URLs or with AD url to resolve LDAP URL -->
<urls>
<url>example.com</url>
</urls>
<referral>ignore</referral>
<ignore_partial_result_exception>false</ignore_partial_result_exception>
<!-- only for AD. necessary for login with sAMAccountName -->
<domain>example.com</domain>
<manager_user>...</manager_user>
<manager_password>...</manager_password>
<user_search_filter>(&(objectclass=user)(memberOf=CN=development,OU=development,OU=example_company,DC=example,DC=com))</user_search_filter>
<!-- default: false - values: true/false -->
<search_subtree>true</search_subtree>
<group_search_filter>(&(objectclass=group)(member={0}))</group_search_filter>
<group_search_result>dn</group_search_result>
<!-- URL to external single sign-on service -->
<single_sign_on_url>https://sso.example.com/example-sso</single_sign_on_url>
<single_sign_on_visible>false</single_sign_on_visible>
<single_sign_on_order>20</single_sign_on_order>
</authentication_provider>
